Cybercrime is on the rise, and the pandemic hasn’t helped the problem. “Cybercriminals are developing and boosting their attacks at an alarming pace, exploiting the fear and uncertainty caused by the unstable social and economic situation created by COVID-19,” says Jürgen Stock, INTERPOL Secretary-General.
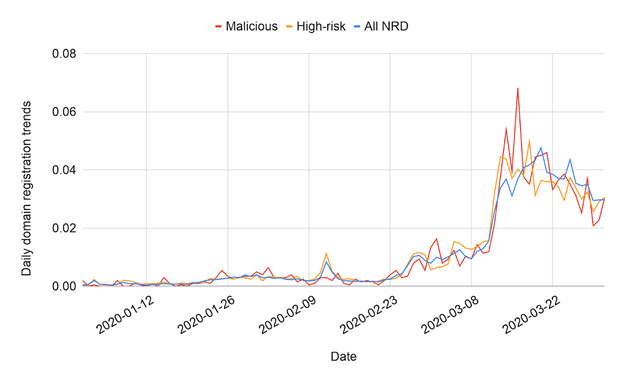
February to March of 2020 saw a huge rise in malicious and high-risk coronavirus-related domain registrations: Image Source
But what does cybercrime have to do with fleet management?
Well, there are multiple ways cybercriminals can gain access to private information – including fleet management data. They could hack into a fleet’s GPS systems or access the control unit itself with relatively cheap GPS spoofing tools used to create fake GPS signals.
Once they’ve gained access, they can take control of a fleet and its data, leaving it vulnerable to theft. This poses a threat to both your assets and drivers’ safety.
It’s vital fleet managers protect their data now and as we emerge from the pandemic. Let’s take a closer look at what cybercrime is, how it affects fleets, and how to keep your data and drivers safe.
What is Cybercrime?
Cybercrime is any law-breaking activity that’s conducted through a computer – including fraud, stealing intellectual property, or violating privacy.
It’s been on the rise over the past few years as criminals have become more intelligent in their efforts to steal information.
Cybercrime takes various forms, from social engineering to data theft – and fleet managers should make it a priority to learn about each kind and how it could affect their fleet.
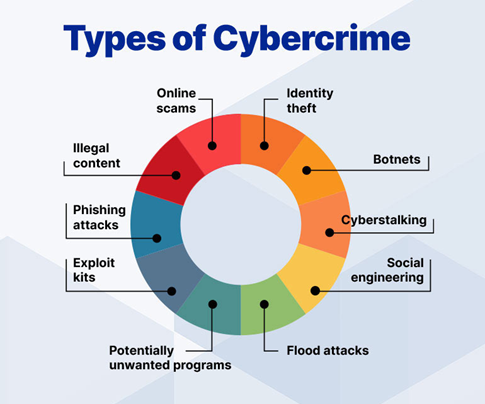
Types of Data Most Commonly Stolen
From card details to identify theft, cybercrime comes in a variety of guises. Here are some of the most common types of attacks.
Payment Data
Stealing payment data is a form of money theft. It could include siphoning bank accounts or selling payment card details.
Authentication Data
Getting into online systems gives criminals access to personal data. It’s also a foot in the door for things like extortion and payment data.
Copyrighted Material
Instead of paying for information, cybercriminals can log into company systems and steal software and other business-critical data.
Classified Information
Whether the information in your business is top secret or just sensitive, having it fall into the wrong hands could spell big trouble.
The Effects of a Cyber Attack on Your Fleet
When a cyberattack happens, organizations typically go through several stages of disruption. From bad PR to huge legal fines, an attack could wreak havoc.
After the damage occurs, managers need to act quickly to minimize its impact. This takes them away from their usual responsibilities, potentially bringing the company to a halt. There are assets and information to recover, potential litigation to deal with, and the company’s reputation to manage. All of this can be incredibly costly.
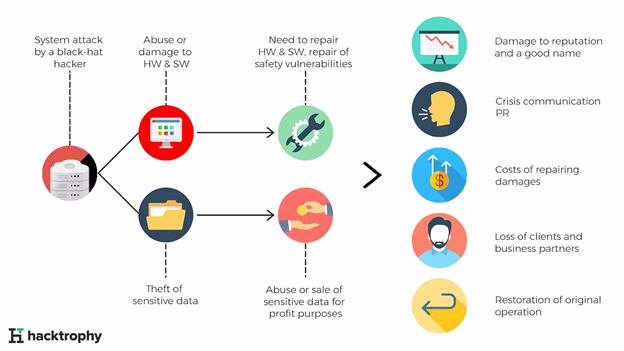
How to Protect Your Fleet from a Cyberattack
It’s impossible to remove all the risks when it comes to cybercrime. However, fleet managers should be carrying out regular vulnerability assessments to identify potential weaknesses.
Risk assessments can help managers identify mission-critical components (the tasks that would be impacted most in the event of a cyberattack) and then implement steps to protect these activities. That way, if an attack occurs, the business will be better prepared to keep these activities running.
Here are some steps you can take:
- Understand the risks and communicate them to stakeholders in your business.
- Make security a part of your organizational culture by focusing on compliance, best practices, and good communication.
- Take steps to minimize the risk of data theft. For example, invest in secure digital systems rather than relying on paper documents.
- Set strong passwords and back up your data, especially for your fleet management software.
- Choose your software wisely. Technology should come with password protection options to keep data safe and secure.
- Keep software updated. Updates often come with improved security features that will help better protect your data.
- Control access to vehicles with locks, fleet tracking, and careful scheduling. This will help keep track of who has access to the vehicles and their software.
- Finally, test your systems to identify how exploitable they are and the impact of a breach. Preparation is the key to minimizing impact, so the more of it you can do, the safer you’ll be.
With these steps in place, you can rest assured that your business is taking the proper precautions to keep your data safe and secure.
To find out more about GPS fleet management software, your data, and how to keep it protected, request our Powerfleet (formerly Fleet Complete) demo today.